How to validate findings?
Don't take everything for granted. Manually verify your findings before generating the final report.
Why not automate 100% of the process?
Because you just can’t automate everything. No automated scanner can...
- Interpret the context of the target
- Decide which data is important
- Know when to stop or when to push further
- Find logic flaws, chain exploits, and do custom post-exploitation
🚀 We highly recommend Pentest-Tools.com users go through all the reported vulnerabilities and manually verify them.
To make this task easier for you, our scanners can automatically verify some findings by exploiting the identified vulnerabilities and presenting the user with a proof of exploitation. These will be already tagged as CERTAIN.
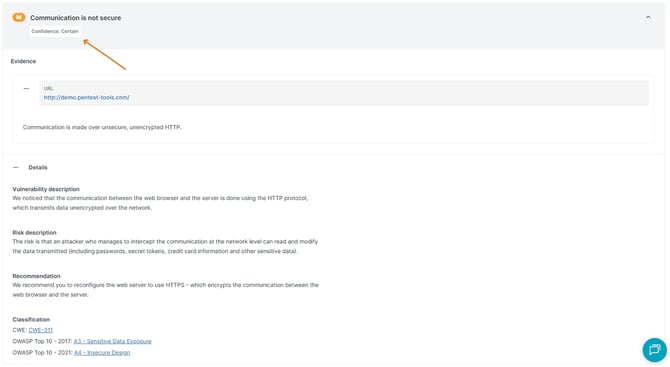
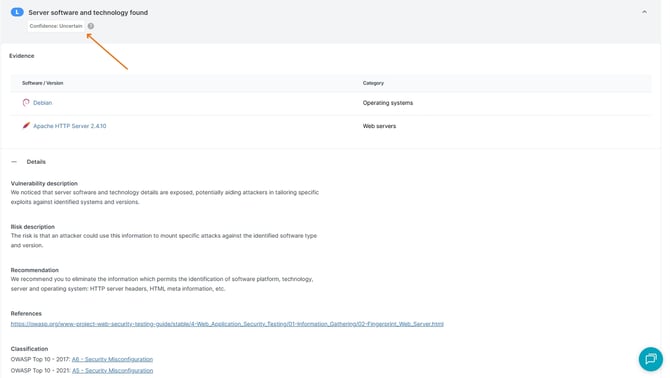
The findings that cannot be automatically validated will be tagged as UNCERTAIN. This means that they may or may not be legitimate findings, as such is the inherent risk of any automated scanner - to generate false positives.
Our development team is doing its best to reduce the rate of false positives generated by the scanners, as well as provide as much information as possible in the finding details section, so you can manually check and confirm each finding.
To help you manually validate findings we provide an easy exploit that runs the attack vector directly from the scan result. Use the Replay Attack button to check the result of the exploit.

You can also run one of our dedicated exploit tools to verify findings, such as Sniper - Automatic Exploiter, SQLi Exploiter, or XSS Exploiter.
Once verified, you can go to your findings tab, select the finding(s), and click Change Verified.
If a particular finding cannot be manually confirmed by yourself, based on the details and payloads we provide on the finding or the use of additional offensive tools, then there is a chance that it is a false positive. See here how to mark a finding as a false positive to automatically exclude it from reports and any future scans.
You can order some consultation hours and one of our certified penetration testers can assist in manually checking all the findings that you have doubts about.