Webhook Integration
Webhooks allow you to trigger outgoing HTTP POST requests from Pentest-Tools.com to your endpoints whenever certain events have happened.
Last Updated: March 31, 2025
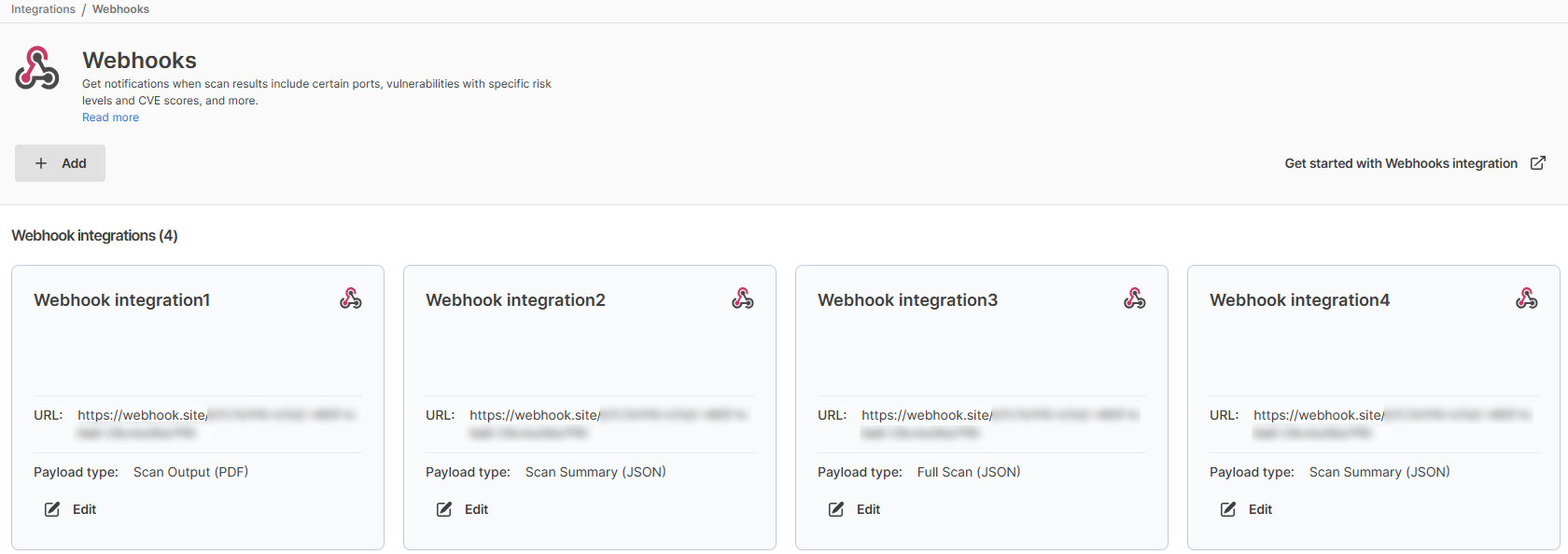
To create a webhook go to your Pentest-Tools.com dashboard and find the integrations menu on the sidebar. Here you can configure integrations with 3rd-party apps which you can later use for notifications (Slack, Webhooks), or vulnerability management workflows (JIRA). More integrations will be added in the future.
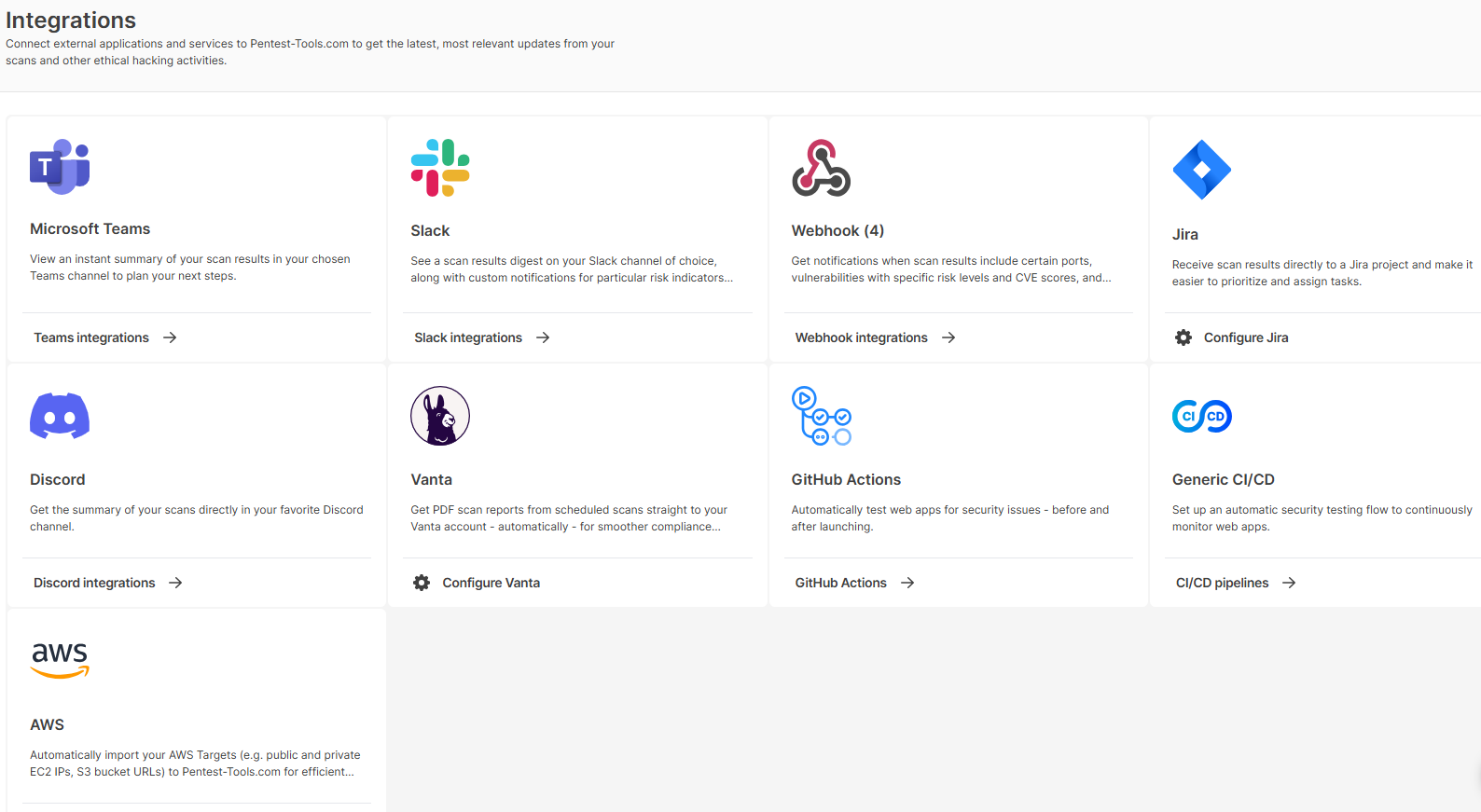
When you enter the webhook configuration, click + Add New and a window will open containing 4 categories:
- Webhook name - here you will fill in the name of the webhook you will create
- Webhook description - here you will fill in a description that will help you understand in the future what that webhook does
- Webhook URL - here you will fill in the URL to which the webhook will send the data to
- Webhook Payload Type - here you will choose what kind of data to be sent to the Webhook URL
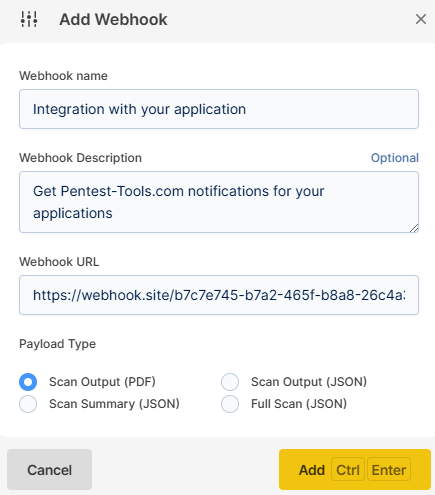
There are 3 kinds of data (Webhook Payload Type) that you can send:
- Scan Output (PDF)
- Scan Output (JSON)
- Scan Summary (JSON)
Each one of these 3 options allows you to send a type of payload to the specified URL whenever a selected event occurs.
Also, multiple webhooks can be created from this page so you can send data to multiple endpoints.
After adding a new webhook, you can use it by configuring a new Notification and enabling the webhook action. Here are some examples of how the webhook payload type will look like, for each of the 3 options:
1. The PDF output is a standard scan result, see here a sample report.
2. Scan output JSON - see an extract below
[
{
"id": 73018480,
"name": "Vulnerabilities found for server-side software",
"test_id": 8,
"test_name": "default",
"test_description": "Checking for vulnerabilities of server-side software...",
"test_finished": true,
"cve": "",
"cvss": "-1",
"cwe": "CWE-1026",
"owasp2013": "A9 - Using Components with Known Vulnerabilities",
"owasp2017": "A9 - Using Components with Known Vulnerabilities",
"vuln_description": "Vulnerabilities found for server-side software",
"vuln_evidence": {
"type": "table",
"data": [
[
"<b>Risk Level</b>",
"<b>CVSS</b>",
"<b>CVE</b>",
"<b>Summary</b>",
"<b>Exploit</b>",
"<b>Affected software</b>"
],
[
"<i class='ace-icon fa fa-circle red'></i>",
7.5,
"<a href='https://nvd.nist.gov/vuln/detail/CVE-2017-3167' target='_blank'>CVE-2017-3167</a>",
"In Apache httpd 2.2.x before 2.2.33 and 2.4.x before 2.4.26, use of the ap_get_basic_auth_pw() by third-party modules outside of the authentication phase may lead to authentication requirements being bypassed.",
"N/A",
"http_server 2.4.25"
],
[
"<i class='ace-icon fa fa-circle red'></i>",
7.5,
"<a href='https://nvd.nist.gov/vuln/detail/CVE-2017-3169' target='_blank'>CVE-2017-3169</a>",
"In Apache httpd 2.2.x before 2.2.33 and 2.4.x before 2.4.26, mod_ssl may dereference a NULL pointer when third-party modules call ap_hook_process_connection() during an HTTP request to an HTTPS port.",
"N/A",
"http_server 2.4.25"
],
[
"<i class='ace-icon fa fa-circle red'></i>",
7.5,
"<a href='https://nvd.nist.gov/vuln/detail/CVE-2017-7668' target='_blank'>CVE-2017-7668</a>",
"The HTTP strict parsing changes added in Apache httpd 2.2.32 and 2.4.24 introduced a bug in token list parsing, which allows ap_find_token() to search past the end of its input string. By maliciously crafting a sequence of request headers, an attacker may be able to cause a segmentation fault, or to force ap_find_token() to return an incorrect value.",
"N/A",
"http_server 2.4.25"
],
[
"<i class='ace-icon fa fa-circle red'></i>",
7.5,
"<a href='https://nvd.nist.gov/vuln/detail/CVE-2017-7679' target='_blank'>CVE-2017-7679</a>",
"In Apache httpd 2.2.x before 2.2.33 and 2.4.x before 2.4.26, mod_mime can read one byte past the end of a buffer when sending a malicious Content-Type response header.",
"N/A",
"http_server 2.4.25"
],
[
"<i class='ace-icon fa fa-circle red'></i>",
7.5,
"<a href='https://nvd.nist.gov/vuln/detail/CVE-2021-26691' target='_blank'>CVE-2021-26691</a>",
"In Apache HTTP Server versions 2.4.0 to 2.4.46 a specially crafted SessionHeader sent by an origin server could cause a heap overflow",
"N/A",
"http_server 2.4.25"
],
[
"<i class='ace-icon fa fa-circle orange'></i>",
4.3,
"<a href='https://nvd.nist.gov/vuln/detail/CVE-2015-9251' target='_blank'>CVE-2015-9251</a>",
"jQuery before 3.0.0 is vulnerable to Cross-site Scripting (XSS) attacks when a cross-domain Ajax request is performed without the dataType option, causing text/javascript responses to be executed.",
"N/A",
"jQuery 2.1.4"
],
[
"<i class='ace-icon fa fa-circle orange'></i>",
4.3,
"<a href='https://nvd.nist.gov/vuln/detail/CVE-2019-11358' target='_blank'>CVE-2019-11358</a>",
"jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.",
"N/A",
"jQuery 2.1.4"
],
[
"<i class='ace-icon fa fa-circle orange'></i>",
4.3,
"<a href='https://nvd.nist.gov/vuln/detail/CVE-2020-11022' target='_blank'>CVE-2020-11022</a>",
"In jQuery versions greater than or equal to 1.2 and before 3.5.0, passing HTML from untrusted sources - even after sanitizing it - to one of jQuery's DOM manipulation methods (i.e. .html(), .append(), and others) may execute untrusted code. This problem is patched in jQuery 3.5.0.",
"N/A",
"jQuery 2.1.4"
],
[
"<i class='ace-icon fa fa-circle orange'></i>",
4.3,
"<a href='https://nvd.nist.gov/vuln/detail/CVE-2020-11023' target='_blank'>CVE-2020-11023</a>",
"In jQuery versions greater than or equal to 1.0.3 and before 3.5.0, passing HTML containing <option> elements from untrusted sources - even after sanitizing it - to one of jQuery's DOM manipulation methods (i.e. .html(), .append(), and others) may execute untrusted code. This problem is patched in jQuery 3.5.0.",
"N/A",
"jQuery 2.1.4"
]
]
},
"risk_description": "These vulnerabilities expose the affected applications to the risk of unauthorized access to confidential data and possibly to denial of service attacks. An attacker could search for an appropriate exploit (or create one himself) for any of these vulnerabilities and use it to attack the system.",
"risk_level": "3",
"screenshots": null,
"status": 0,
"recommendation": "We recommend you to upgrade the affected software to the latest version in order to eliminate the risk of these vulnerabilities.",
"vuln_references": null,
"vuln_id": "WEBSCAN-00-0000002",
"finding_verified": false,
"confirmed": false,
"port": null,
"protocol": null
},
3. Scan summary JSON
{
"id": 19072382,
"target_id": 14276739,
"tool_id": 170,
"status_name": "finished",
"vpn_scan": false,
"progress": 100,
"result_summary": {
"high": 1,
"medium": 1,
"low": 6,
"info": 11,
"text": ""
},
"start_time": "2022-06-13 13:31:11",
"end_time": "2022-06-13 13:31:28",
"duration": 17,
"num_tests": 19,
"num_finished_tests": 19
}
To learn more about notifications, please see our dedicated support category.